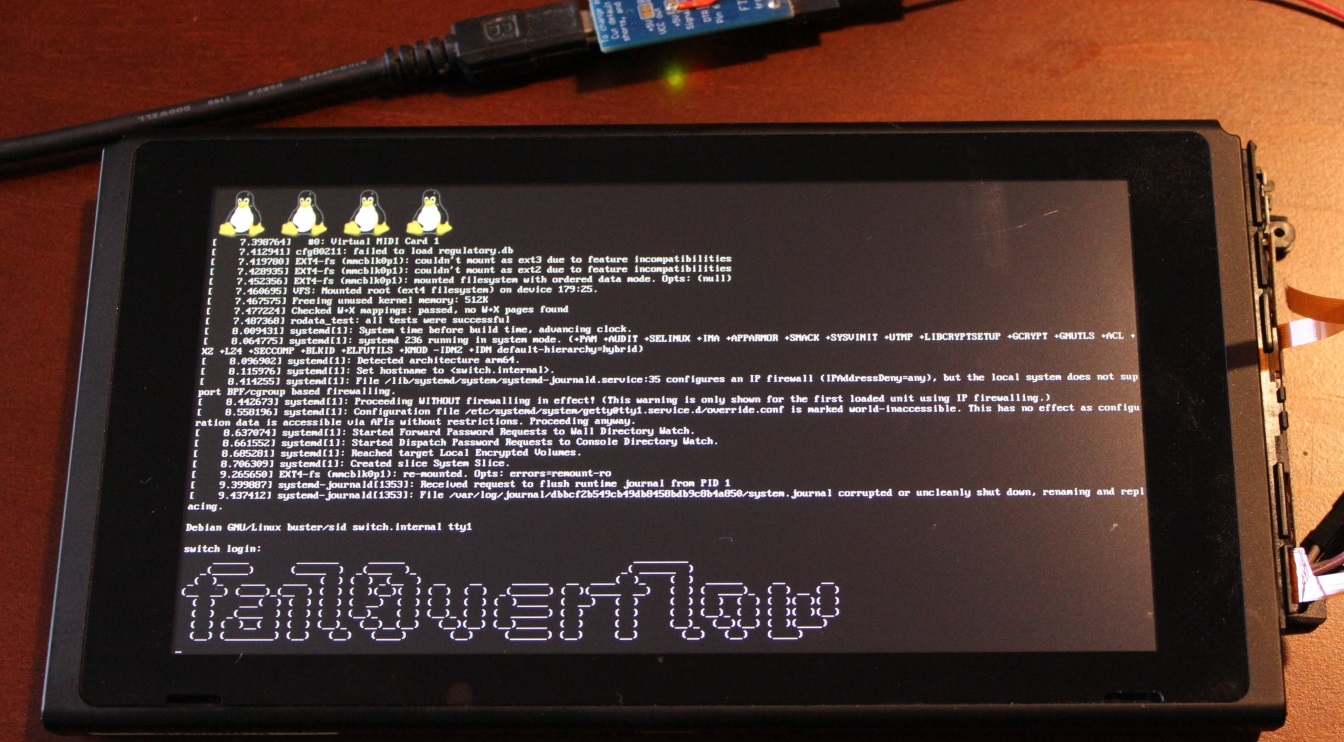
Hackers’ accelerating efforts to get full control of the Nintendo Switch, allowing the popular system to run homebrew code and, potentially, pirated games. This week, the hacking team fail0verflow claimed a major advance in that effort, tweeting a picture showing Linux booting up on the machine.
While fail0verflow’s photo wouldn’t be that difficult to fake, the group has released several significant hacks for systems ranging from the Wii to the PS4 in the past, lending credence to their Switch hacking claims. Fail0verflow previously tweeted video of a homebrew “scroller” animation running on the Switch, and the group claimed its code exploit worked in a way that “can’t be patched (in currently released Switches).”
Despite the public tease, it might be a while before fail0verflow releases details and code for its Switch exploit to the public. While fail0verflow demonstrated a Linux port for the PS4 in 2016, the team didn’t reveal the PS4 exploit it used to run that code until over a year later, by which point the exploit had been patched out of more modern PS4 firmware. And the presence of some external hardware, wires, and ribbon cables in fail0verflow’s photo suggest the Switch exploit might not even be possible on unmodified hardware just yet.
Meanwhile, progress has continued in other portions of the Switch hacking community since a security conference presentation effectively blew the console’s security wide open late last year. Dedicated hackers have now fully documented the internal “NCM services” codes that allow for file path and content management on the system and released an accompanying module for coders to access them. A separate “hactool” release allows hackers to easily “view information about, decrypt, and extract common file formats for the Nintendo Switch,” though using that tool requires its own hacked access to some internal decryption keys.
A self-contained homebrew launcher that hacker plutoo previously teased for Feb. 1 release has since been “delayed for 2 weeks,” though, because “something came up,” according to a tweet.
For those with deep technical knowhow, hacker SciresM has posted detailed breakdowns of how to access the Switch’s high-level “TrustZone” security layer and how to extract public RSA keys from the system. Or, if you prefer the white hat route, Nintendo is still offering bounties for reports of system vulnerabilities via HackerOne.